CI/CD Security vs. Security-as-Code: which lowers risk more?
Vulnerability injections in the CI/CD pipeline recently led to open source projects making headlines. Here’s a better way to secure.
Learn moreReady for a demo? Contact sales

Swiftly identify and precisely resolve vulnerabilities in real-time, ensuring your apps and APIs remain resilient against ever-evolving cyber threats.
Waratek Secure delivers speed, accuracy, and resilience in Java applications & APIs. Swiftly identify and precisely resolve vulnerabilities in real-time, ensuring your systems remain resilient against ever-evolving cyber threats.
Waratek's Java Security Platform not only found the cryptominer we had, but securely removed it within 48 hours, stopping us from having to rebuild our solution from scratch.
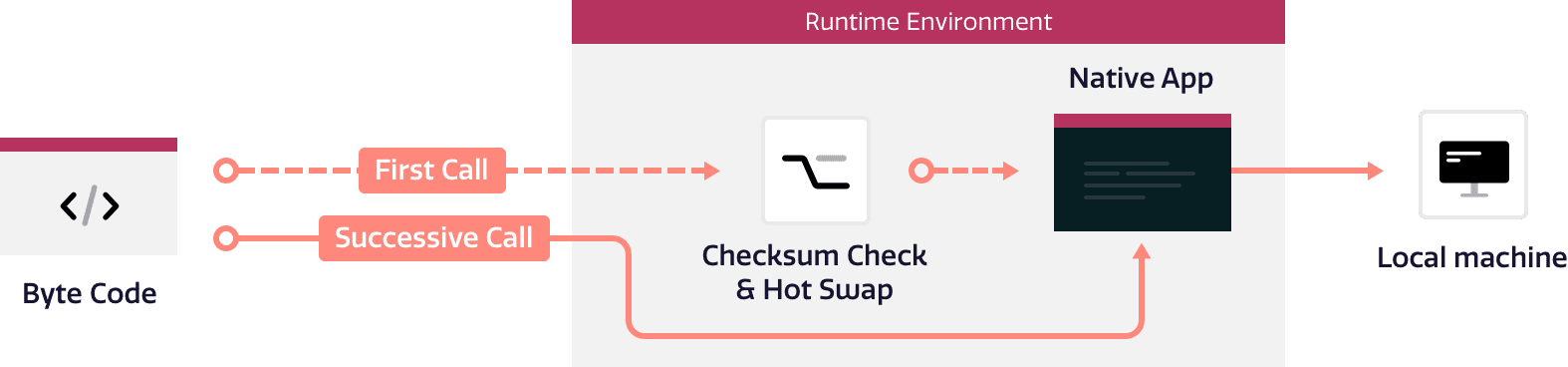
In the rapidly evolving digital landscape, a static security approach is no longer adequate.
Waratek Secure offers real-time dynamic patching capabilities through our unique, enterprise-grade engine. This engine operates on the principles of proactive discovery and immediate resolution.
Once the target function and the corresponding location-specifier within that function are identified, Waratek Secure applies the patch instantaneously.
The result? Immediate remediation of code vulnerabilities, eliminating the need for manual intervention or system downtime.

Traditionally, applying patches has required time-consuming code changes, system restarts, and even complete application redeployments.
Waratek Secure allows for dynamic remediation of vulnerabilities without any code changes. This means that your teams can apply necessary security rules without the labor-intensive process of changing and testing code to significantly save time and resources.
This revolutionary approach to patching and vulnerability remediation breaks down the traditional barriers faced by security teams, marking Waratek Secure as the vanguard of secure, seamless, and uninterrupted application performance.

Signature-based security solutions can often raise false alarms, causing unnecessary disruptions and resource allocation. Waratek Secure transcends this challenge with the Java Security Platform.
The Java Security Platform prevents false positives by employing a meticulous ledger inside the memory of the JVM. This ledger logs when and where untrusted data enters the system from the network and is used by vulnerable code.
When an exploit is detected, it's not only logged, but the vulnerable code is also compiled out. This unique approach renders the untrusted data benign as the vulnerability it was meant to exploit no longer exists.
With Waratek Secure, you are not just implementing a security solution; you're fortifying a future where your applications are consistently secure, relentlessly efficient, and unconditionally trustworthy.

Modern enterprises heavily depend on applications with RESTful API endpoints, becoming potential targets for cyberattacks. To mitigate this risk, Waratek Secure brings a new level of safety to your APIs, assuring peace of mind while enabling seamless operation of your applications.
Our unique API discovery feature sheds light on your digital landscape by detecting exposed RESTful API endpoints and delivering this vital information to the Waratek Portal.
Waratek Secure utilizes the same robust engine that powers our unrivalled application security to bolster your Java APIs' defenses. We deliver an unprecedented level of accuracy in API security, providing your enterprise with the resilience it needs in an increasingly connected world.
Can't find the answer you’re looking for? Reach out to our sales team.
If Waratek Secure fails to locate the target function within the JVM, the patch rule will not be applied and no linking event for that rule will take place.
The link state provides important cues about the functioning of your Waratek Secure rule. If no link states are visible in the event log when expected, it may signal an error in the function statement or location-specifier. This helps you identify and rectify potential issues promptly.
If an uncaught exception is thrown from the patch method, Waratek Secure considers the patch rule to be defective and immediately unlinks the rule from the target function, effectively preventing any potential adverse effects on your application's operation.
Waratek Secure patches can return a value from the patched function, halting further bytecode instructions post patch application. This allows for precise control over application behavior following the application of a patch.
The JavaFrame API provides a range of methods for reading and writing values stored in specific indices of the local variable array or the operand stack. This empowers you to manipulate data within your functions with great precision.
Absolutely. With its ability to apply patches in real-time and at any point of JVM execution, Waratek Secure offers an effective solution for rapidly addressing newly discovered vulnerabilities and ensuring ongoing application security.
Waratek Secure has the capability to link and apply patches whenever the matching function and location-specifier are loaded into the JVM, not just during application startup. This allows for dynamic and timely patch application throughout the application's runtime.
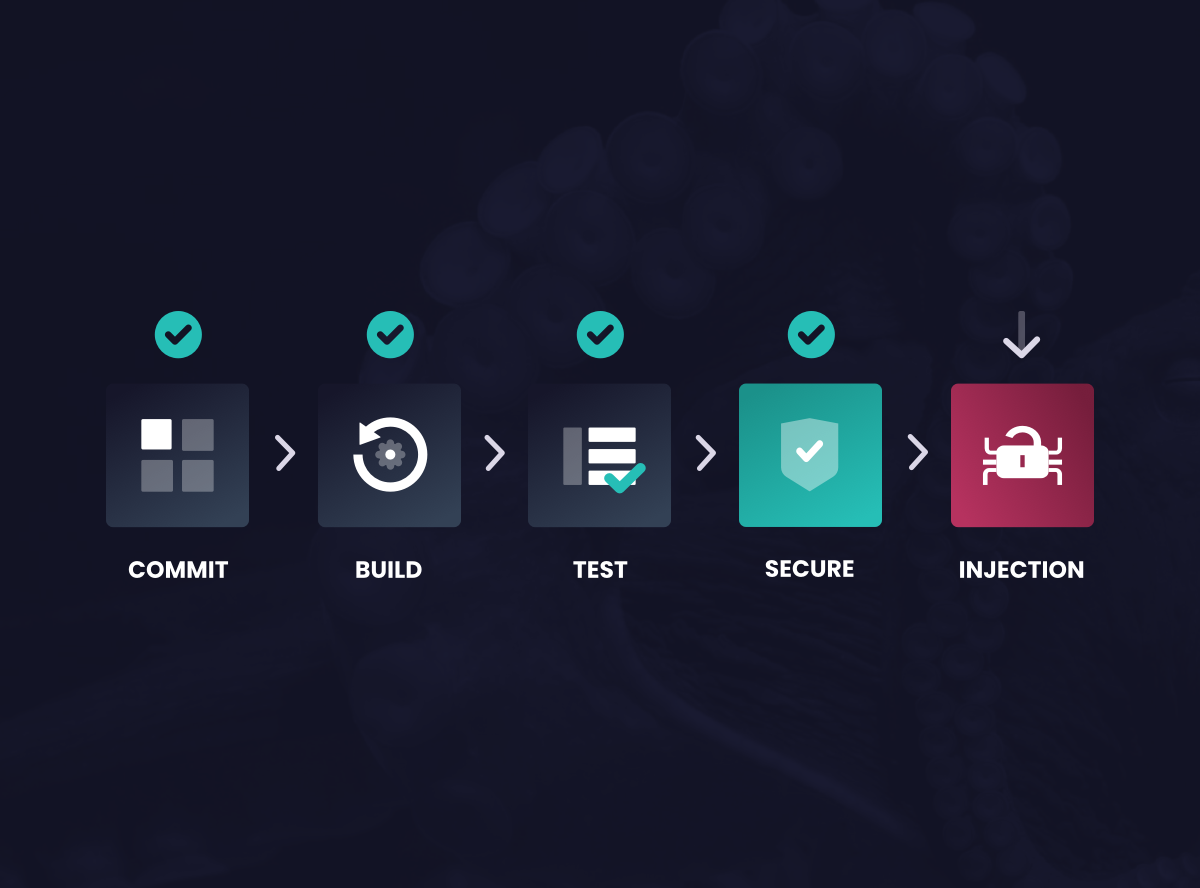
Vulnerability injections in the CI/CD pipeline recently led to open source projects making headlines. Here’s a better way to secure.
Learn moreWork with us to accelerate your adoption of Security-as-Code to deliver application security at scale.