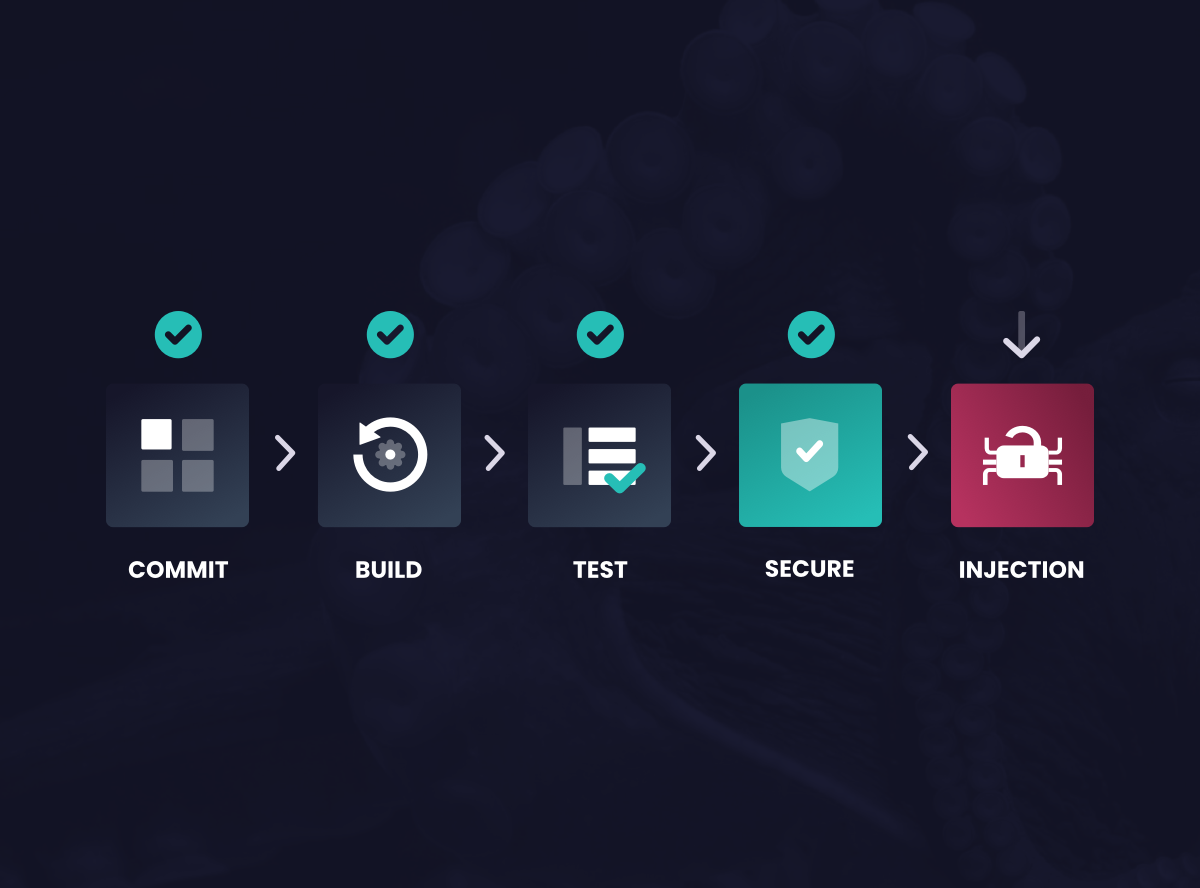
The solution
Using Waratek’s Security-as-Code platform and turning on the declarative “Deserial” rule wholly and automatically protects the entire application stack against Java deserialization attacks, known or unknown (zero-day).
Waratek achieves this level of protection by creating a dynamic, restricted compartment inside its platform. This restricted compartment is active for the duration of each deserialization operation and afterward, such as during garbage collection. The restricted compartment allows any legitimate functionality to run normally but prohibits any gadget chain from abusing and compromising the system. The feature allows the InvokerTransformer to be used generally by systems that depend on this functionality without compromising the system by any malicious gadget chains.